Ever found your website was getting sluggish? Or worse, that your site was suddenly and totally inaccessible to users? You might’ve been totally stumped by the cause –– you haven’t made a recent marketing push or done anything else that would slow down servers. One possible cause is what’s known as a Distributed Denial of Service attack (“DDoS” for short).
Let’s look at a few basic questions — like what are DDoS attacks, how to detect DDos, how to prevent a DDos attack, and how to report a DDos attack.
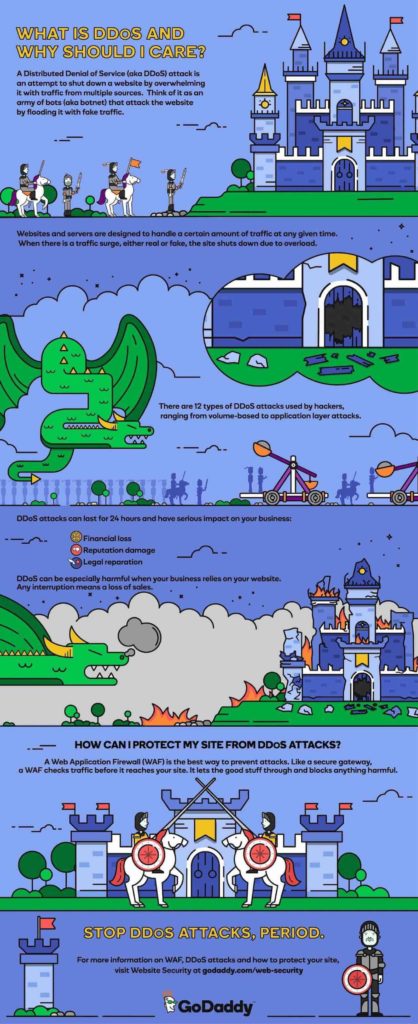
What are DDoS attacks?

In strictly technical terms, distributed denial of service is when someone attempts to bring down a website by flooding a part of it with so much traffic that the server eventually crashes (that’s the “denial of service” part, as the site’s users are denied service).
Because websites have so many moving components, hackers have devised a few different types of DDoS attacks, aimed at different layers:
Volume-Based Attacks are the bread-and-butter of botnets. They simply attempt to consume more bandwidth than the server can provide. If you think of a website’s bandwidth as a water source, volume-based attacks siphon off as much of the resource as possible, so there’s none left for anyone else.
Protocol Attacks are more sophisticated and attempt to flood the network with more server requests (commonly referred to as “packets”) than it can handle. A network is like a freeway system: it’s built to handle a certain amount of traffic, and a protocol attack attempts to congest it with more packets than it can handle.
Application Layer Attacks are arguably the most sophisticated. They typically leverage flaws in a website application’s code and abuse it in ways that overwhelm the system. An analogy here is harder to come up with, but imagine tricking an old-school switchboard to make it think that each call it receives actually takes up 10 lines.
To generate the traffic for distributed denial of service, hackers often rely on botnets, or fleets of computers infected with their malware. The hacker tells all the computers in its botnet to repeatedly attempt to load the target website until it crashes. This is where “distributed” comes from. Because the traffic comes from a distributed set of computers, it can look like real traffic because it comes from sources that would otherwise represent real people visiting a website.
As if all that isn’t disheartening enough, some people will build a botnet and then lease it to another party, making distributed denial of service as simple as paying someone else to do the dirty work for you.
Who gets targeted in distributed denial of service attacks?
Why a website gets targeted for a DDoS attack is a lot more complicated than the technical explanation of how it works. For example, a few high-profile companies have recently been brought down by botnets, for a number of different reasons:
- Developer-focused site GitHub experienced an enormous volume-based DDoS in 2015, although GitHub never publicly announced why they think the attack occurred.
- Well-known UK retailer Carphone Warehouse suffered a DDoS attack, which hackers used to divert the company’s attention while a huge trove of their customers’ data was stolen.
- International news outlet Al Jazeera was the target of a recent attack related to its coverage of political events.
While these high-profile cases might make it seem like your website would go unnoticed, attacks are more often conducted against small sites with less sophisticated DDoS-prevention technology. Hackers might pick sites when they have a personal grudge or are trying to ransom the owner into stopping the attack.
Unfortunately, though, there is often a lot of collateral damage with distributed denial of service.
Even those who are in no way related to the targeted website will experience slowness. For example, if you notice that your website is slow, and the traffic is in fact generated by a botnet, it doesn’t mean that you were necessarily the victim. Your website might have simply been hosted on the same server as the website the hacker meant to target.
Protect your site against DDoS attacks
We have some good news, though: For small business owners, there are simple solutions that can protect your website without costing an arm or a leg. You can mitigate mass DDoS attacks by deploying a Web Application Firewall (WAF).
How does WAF work?
A Web Application Firewall examines all traffic approaching your site and applies a set of filters and rules to reject malicious traffic — including malware, bots, XSS (cross site scripting), SQL injection, etc. A WAF like the solution offered by GoDaddy Website Security, can protect your site from botnet traffic surges and other malicious content.
Keeping your site safe also keeps your customers safe and your site’s reputation intact.
Keeping visitors safe should be a top priority of anyone running a website, because hackers are always on the lookout for easy botnet-building targets.
Preventing distributed denial of service
The best place to start? Make sure your website is protected in the first place. While there are many steps you can take, here are some of the most potent:
- Always use complex, secure passwords to prevent hackers from easily entering your site.
- Keep software your website uses up to date. This is crucial for anyone using WordPress and eCommerce software.
- Put in the extra effort to ensure your site remains secure. For example, take basic steps to secure your WordPress website and protect an eCommerce site from hackers.
Don’t forget about DDoS detection
Even with the most stringent security standards, it’s always possible an attacker used a previously unknown exploit to infect your site. The best way to ensure your site has never been compromised is to regularly check all of its files for suspicious content.
One of the easiest ways to do this is with GoDaddy’s Website Security, which does all the heavy lifting for you at a fraction of the price of a security specialist doing the same work.
How to report a DDos attack
If you suspect or have determined that you’re under attack, ICANN (the Internet Corporation for Assigned Names and Numbers), recommends that you first contact your hosting provider. Then contact your internet service provider. Be sure to quickly explain that you’re under DDos attack so they can route your call quickly to the right department.
A quick recap
To make sure you got the most important parts of the article, here’s what we covered:
- Distributed Denial of Service (DDoS) attacks use computers infected with malware (known as botnets) to flood a site with traffic, which will stop it from working.
- Big companies aren’t the only victims of DDos attacks. In fact, small websites with less sophisticated DDoS-prevention technology are targeted more often..
- A Web Application Firewall (WAF) can protect your website against malicious traffic of many sorts, including DDoS attacks and malware.
- Be proactive by regularly scanning your site for security concerns. A tool like GoDaddy Website Security can do the heavy lifting for you.
- Bottom line: You need to protect your site from being infected and distributing malware to your visitors, preventing them from becoming part of a botnet.
Armed with that knowledge, we hope you can go forward and make the internet a safer and better place for your visitors and everyone else!






