In the past years, malware attacks evolved became very sophisticated. Their growth has to be taken into consideration by internet users especially business owners.
Every day, we can read about the release of a new malware attack in the hacking news and public cyber security magazines. So, what is more important for business security and continuity? Is it being aware of new malware types and releases? Or Is it taking an action to prevent malicious files and activities made by cyber criminals?
In this article, we will discuss types of malware attacks and how can you protect yourself from them.
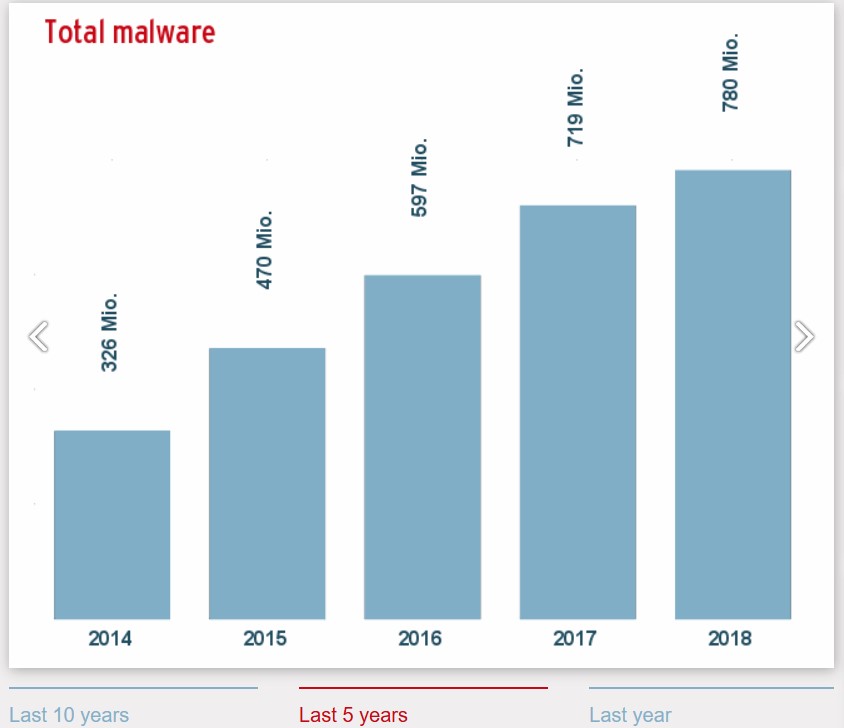
Types of malware attacks
- Virus
- Worm
- Ransomware
- Crypto miner
- Trojan
- Rootkit
- Adware
- Spyware
- Keylogger
- Spam
- Phishing
- Browser Hijacker
Virus
Virus is a form of malware that is capable of copying itself and spreading to other computers. Viruses often spread to other computers. They attach themselves to programs and executing malicious codes when the user launches one of those infected programs. They can also spread through script files, documents, and cross-site scripting vulnerabilities in web apps. Viruses can be used to steal information, harm host computers and networks, create botnets, steal money, render advertisements, and more.
Worm
Worm is a program that replicates itself and destroys data and files on the computer. it uses computer networks to spread, relying on security failures in the targeted computer to access it, and steal or delete data. Many worms are designed only to spread and do not attempt to change the systems that they pass through.
Ransomware
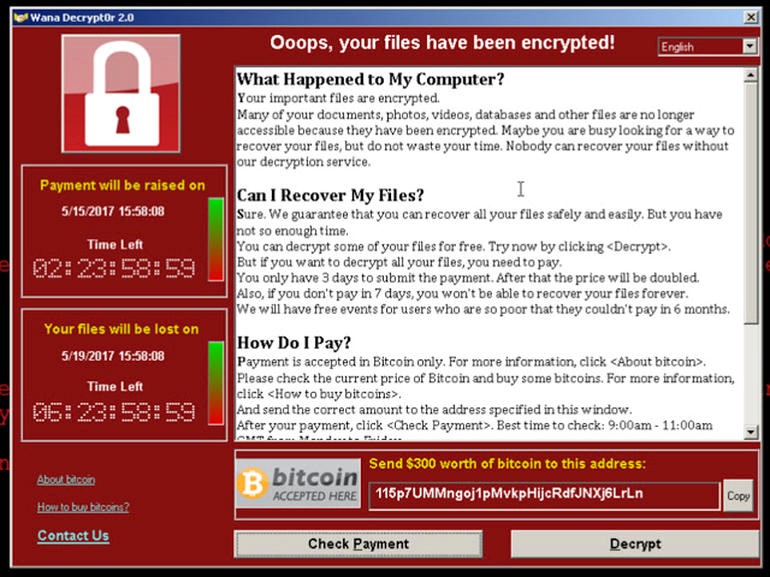
Ransomware is one of the malware attacks that holds a computer system captive while demanding a ransom. You’ll find a message that warns you that your files have been encrypted or you have been locked out of your computer until you pay a ransom for the cyber-criminals. This means that your system is severely infected with a form of Malware called Ransomware.
Ransomware typically spreads like a normal computer worm ending up on a computer via a downloaded file or through other vulnerabilities in a network service.
Crypto miner
Crypto miner is a relatively new term that refers to software programs and malware components developed to take over a computer's resources and use them for cryptocurrency mining without a user's explicit permission.
Cyber criminals are increasingly turned to crypto miner malware as a way to use the processing power of large numbers of computers, smartphones and other electronic devices to help them generate revenue from cryptocurrency mining. A single cryptocurrency mining botnet can net cyber criminals more than $30,000 per month.
Trojan
Trojan is a type of malware attacks that mask itself as a normal file or program to trick users into downloading and installing it. A Trojan can give a remote access to an infected computer. Once an attacker has access to the infected computer, it is possible to steal data (logins, financial data, even electronic money), install more malware, modify files, monitor user activity (screen watching, keylogging, etc), use the computer in botnets for Denial of service attack, and anonymize internet activity by the attacker.
Rootkit
Rootkit is a type of malicious software. It is designed to remotely access or control a computer without being detected by users or security programs. Once a rootkit has been installed it is possible for the malicious party behind the rootkit to remotely execute files, access/steal information, modify system configurations, alter software (especially any security software that could detect the rootkit), install concealed malware, or control the computer as part of a botnet. Rootkit prevention, detection, and removal can be difficult due to their stealthy operation. Because a rootkit continually hides its presence, typical security products are not effective in detecting and removing rootkits.
Adware
Adware is the name given to programs designed to display advertisements on your computer, redirect your search requests to advertising websites and collect marketing data about you. For example, adware typically collects the types of websites that you visit so advertisers can display custom advertisements.
Many consider adware that collects data without your consent to be malicious adware. Another example of malicious adware is intrusive pop-up advertisements for supposed fixes for non-existent computer viruses or performance issues.
Spyware
Spyware is a software that spies on you. It is designed to monitor and capture your web browsing and other activities. Spyware, like adware, will often send your browsing activities to advertisers. Spyware, however, includes capabilities not found in adware. It may, for example, also capture sensitive information like banking accounts, passwords, or credit card information.
While not all spywares are malicious, it is controversial because it can violate privacy and has the potential to be abused.
Key logger
Key logger is a software that records everything you type on your computer to glean your log-in names, passwords, and other sensitive information, then send it to the source of the keylogging program. They are often used by corporate and parents to acquire computer usage information.
Spam
Spam is the electronic sending of mass unwanted messages. The most common medium for spam is email, but it is not uncommon for spammers to use instant messages, texting, blogs, web forums, search engines, and social media. While spam is not actually a type of malware, it is very common for malware to spread through spamming. This happens when computers that are infected with viruses, worms, or other malware are used to distribute spam messages containing more malware.
Phishing
Phishing is a cybercrime where a target is contacted by email, telephone or text message by someone posing as a legitimate institution to lure the victim into providing sensitive data, such as personally identifiable information, banking, and credit card details, and passwords.
Technically, phishing is not a malware type, but rather a delivery method that criminals use to distribute many types of malware. We have listed it here among malware types because of its importance and to understand how it works.
Browser Hijacker
Browser Hijacker is when your homepage changes to one that looks like this in the image below:
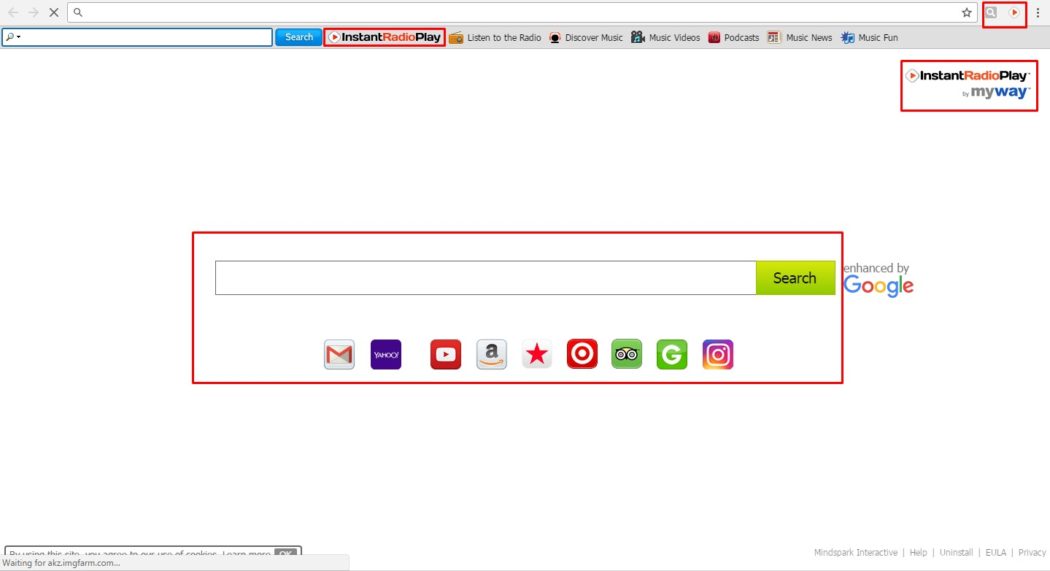
You may have been infected with one form or another of a Browser Hijacker. This dangerous Malware will redirect your normal search activity and give you the results the attackers want you to see. Its intention is to make money off your web surfing. Using this homepage and not removing the Malware lets the attackers capture your surfing interests. This is especially dangerous, if you use online banking or eCommerce website to shop online.
How can you protect yourself from malware attacks?
- Use a reliable anti-malware software as a basic protection for your device. You can also consider including a proactive cyber security solution as a second layer of defense for maximum protection like GoDaddy’s Express Malware Removal tool.
- Always keep your software patched and up to date, including the operating system and every application you’re using on daily basis.
- Keep a backup with all your important data and your website’s data on external sources like a hard drive, storage or on the cloud.
- Be very cautious! Don’t open emails or click on suspicious files/attachments.
- Use strong and complex unique passwords, a password management system can help you too.
- Always secure your browser while navigating the Internet and browse secure websites that include only SSL certificates when you are using your sensitive information like credit card and passwords.
Remember that security is not just about using a solution, it’s also about improving your online habits and knowledge and being aware of the new malware attacks that can affect you.
Your knowledge of security basics will help you spot online threats easily; delivered via emails, social engineering attacks or any other method attackers may use.