As India’s internet base continues to grow, the rise in cyber-attacks has become a matter of concern. If you want to keep your business systems and personal data safe from hackers and phishers, you need to know how to secure your login credentials data. Two-factor authentication is a faster, more secure way to log in to your accounts.
New forms of attack hit the headlines every week. Did you know that data breaches have cost Indian companies an average of Rs 17.6 crore in 2022 so far?
Hackers have adopted multiple ways of extracting confidential data from companies such as:
- SQL injection
- Bot attacks
- Ransomware
- Malware
In this article, we'll explain why you should be using two-factor authentication and how to activate it for your business.
What is two-factor authentication?
Two-factor authentication (2FA) is a form of multi-factor authentication that requires two steps to verify your identity. In comparison to simply providing an ID and password, two-factor authentication requires you to provide:
 Something only you know (like an answer to a secret question)
Something only you know (like an answer to a secret question)- Something you are (like your fingerprint) or
- Something you have (like a physical token generator) as an additional authentication factor to granting you access to the system
It means that even if someone steals your password, they still won't be able to access your account without the extra security measure. After all, a hacker is unlikely to have both your password and your fingerprint.
Related: The six things you must know to improve information security
Examples of two-factor authentication
There are primarily three types of identifying factors that are most widely used to verify the identity of your employees or customers before allowing them access to your web apps or secure IT systems.
1. Knowledge factor
A knowledge factor can be defined as identifying secret information that is privy only to the user.
Some of the examples of knowledge factors are as follows:
- Unique passphrases
- Answers to secret questions (such as “what is your city of birth?”)
You may have generally encountered the knowledge factor authentication while resetting your bank account passwords or PIN etc.
2. Inheritance factor
An inherence factor is a way to verify a person’s identity by a natural characteristic like face or fingerprints.
The inherence factor is generally the second factor in the two-factor authentication process.
Since no two individuals have the same fingerprints, the inheritance factor enhances the security of the system. It protects against any data breach in case of any leaks of login credentials.
3. Possession factor
A possession factor refers to something you have, like a tangible code authenticator that is in your physical possession, and nobody else has access to the hardware registered for authentication.
The user first enters his/her username and password and then uses the device as the second factor in the authentication process.
Companies dealing with confidential data provide their users with an external token authenticator for implementing two-factor authentication.
Some examples of possession factors include:
- One-time password (OTP) generated by authenticator apps on your mobile device
- Hardware tokens
- Other ID cards
Related: NEW GoDaddy website security – the complete security solution
Difference between two-factor authentication and two-step verification
Before understanding the difference between two-step verification and two-factor authentication, we must understand the similarity between the two.
Both add an extra layer of security beyond the traditional username and password combination.

But the way these two verification processes accomplish this differs in terms of how this additional security layer is added.
Two-step verification is a two-step process that employs two levels of control to verify the identity of a user before granting them access to a secure system. It typically involves identifying two pieces of information that the user knows, like a password and an OTP received via text message.
Two-factor authentication, on the other hand, is a separate authentication process that involves using two separate factors to authenticate the user.
As mentioned, factors can be things that people know (security questions), possess (token generator device), or attributes that are inherent to the user, like biometric patterns.
Stealing the second factor in two-factor authentication is not as easy for hackers as SIM swapping or intervening text messages to get access to the OTPs sent via text messages.
Related: How to install network firewall security
How do I activate two-factor authentication?
We understood the importance of two-factor authentication, so now let’s see how we can activate the two-factor authentication for various systems:
For GoDaddy
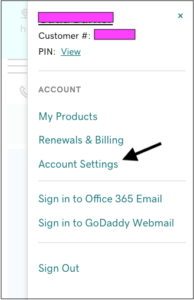
Login into your account and go to Account Settings by clicking your name on the top right corner of the screen. Under Account Settings go to the Login and Pin section and add your 2-step verification.
The three options given by GoDaddy for additional levels of security include:
- Authenticator App (authentication through the GoDaddy app on your mobile device)
- SMS or text message
- Security key (USB encrypted device)
You can choose and configure whichever option that is more convenient to you.
For small businesses
Small businesses can implement two-factor authentication for their employees and users by implementing either of the below:
- Physical security keys: The Yubico Security Key is available for both USB A and USB ports and has one of the best combinations of compatibility and security.
- Software token authentication: You can use third-party authenticator services. The most popular providers of this form of MFA are Google Authenticator, Okta, and PingOne.
For other accounts
Here is a comprehensive guide from Authy that can tell you how to activate two-factor authentication in your favorite apps.
2FA is an easy security win
If you’re not already using two-factor authentication, it’s time to get on board.
2FA can help make sure that your accounts stay safe from malicious cyber-attacks.
You must have heard that any system is as strong as its weakest link. Therefore, try implementing two-factor authentication for your business as soon as possible. This way, attackers won’t be able to access your data — even if they manage to get in by guessing a password or stealing one of the user passwords.