Reverse engineering is the concept of tearing apart an object to see how it works in order to modify the object or make something that can work with it.
Reverse engineering helps recover the design, specifications and functions of the object.
In the software industry, this tactic is widely used to process the software’s binary code and recreate it by tracing back the original source code. This original source code is then used to:
- Study how the program works
- Debug the code
- Improve the functionality of the program
In layman's terms, reverse engineering is like breaking down the parts of a machine to understand the design and functioning of its various parts.
Similarly, if a program was written several years ago and its complete source code is no longer available, then programmers will perform reverse engineering and convert the high-level language that computers understand into a low-level language like Java that humans can understand.
Note: Performing reverse engineering for the purpose of copying or duplicating the program is a violation of copyright laws and can result in penal action.
4 common uses of reverse engineering
Reverse engineering can be used quite legally if done correctly. Here are just four possible applications:
- Software design.
- Software testing.
- IT security.
- Technical documentation.
1. Software design

With the help of reverse engineering, a developer can enhance the functionality of an existing application he or his business owns and add new features. There are different tools and techniques to modify the existing code and add more custom features.
2. Software testing
This tactic is widely used in the field of software testing and for debugging the code. It helps developers to make their way back from the result to the source code in order to easily identify the issues and rectify them.
3. IT security
Reverse engineering is also used by ethical hackers to assess the security of the IT system and highlight any flaws or vulnerabilities that might be used by hackers for harmful activities.
This allows developers to go one step ahead and analyze the malware code to understand the malicious intent of hackers and eliminate flaws in the code.
4. Technical documentation
Large corporates often use old systems and software that are difficult to replace due to operational hassles. The new team members often use reverse engineering in the absence of proper documentation to fully understand the application and its dependencies.
Comprehensive technical documentation can also be prepared for such systems so that other teams can work with the application.
How to conduct reverse engineering for software
Reverse engineering is performed in a set manner. The most important stages are:
Implementation recovery
The initial model which forms the basis of reverse engineering is prepared in this stage. You will read the available documentation and study the database structure of the application.
Design recovery
In this stage, you define unique indexes (unique combinations of data) by identifying the foreign key and candidate key in the data.
Analysis recovery
This is the final phase where you will interpret the model. All artifacts and errors are removed from the model in this stage.
Iteration
There are times when you must iterate between different stages to get the best output. In practice, there is a lot of iteration and backtracking.
To avoid legal issues, especially when working with software or processes that have been patented or trademarked, engineers often use the clean room technique to complete this work.
Tools required for reverse engineering
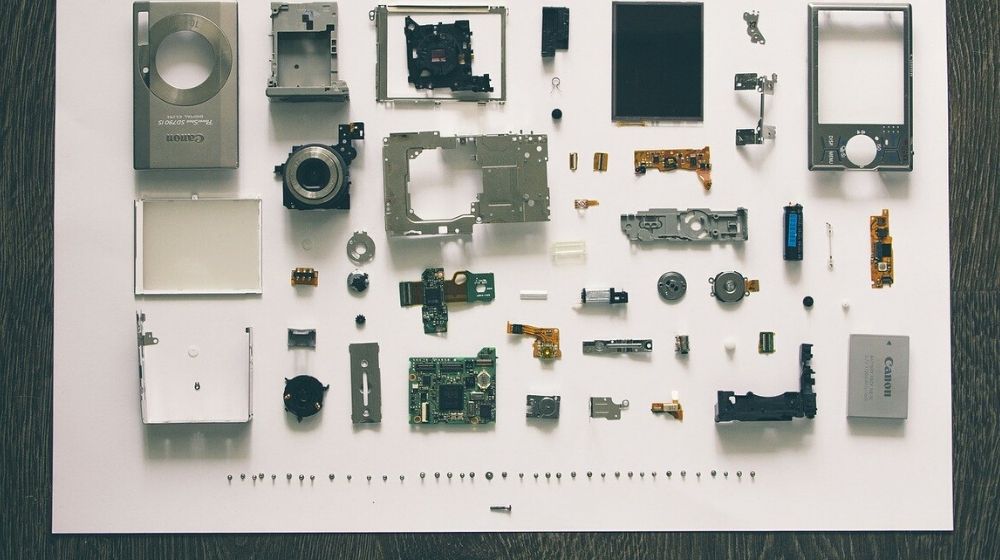
The process involves breaking the component or object into parts in order to analyze the functionality of each. There are a set of tools that help in this process and make the task easier and efficient.
In terms of software, the tools can be categorized into debuggers or disassemblers, hex editors, monitoring and decompile tools:
Disassemblers
Disassemblers are used to convert binary code into a user-friendly format. They are also used to extract strings and imported functions and libraries.
One popular disassembler is IDA Pro. This tool can create maps of the execution to show the binary instructions that are executed by the processor in a symbolic representation called assembly language.
Debuggers
With the help of debuggers, developers can set breakpoints in the program and edit it at the run time. Two examples of debuggers include:
- OllyDbg, a 32-bit assembler level analyzing debugger for Microsoft Windows. Emphasis on binary code analysis makes it particularly useful in cases where the source is unavailable. OllyDbg is a shareware, but you can download and use it for free.
- WinDbg is a multipurpose debugger for the Microsoft Windows computer operating system, distributed by Microsoft.
Hex editors
These editors are used to view the binary language and edit it inside the editor window.
- WinHex which, unlike a simple text editor, can display the code of software files
- Hiew is a popular binary files editor with a built-in disassembler
Monitoring
Tools like API Monitor interpret the API function call and display the input and output data of API call.
Decompile
Decompiler translates the executable version of the program into source code (high-level language). Popular decompiling tools are:
- Procyon, an open-source Java decompiler
- dotPEEK, which can easily compile .NET assembly code into C# source code
Final words

Reverse engineering has many applications, both in the field of hardware as well as software. With the help of various tools, engineers are more empowered to retrieve the source code from the data and perform useful manipulations on it.
Reverse engineering should be used legitimately and any use of reverse engineering for copyright violations should be dealt with strictly.