Even the smallest businesses are finding benefits by installing and using virtual private network (VPN) hardware or software. Why?
- VPNs can extend a business network to include home-based or mobile workers, so those employees can securely access applications, files and other resources on the business network just like they would if they were working in the office.
- VPNs can create a single network that ties together two or more offices securely over the Internet.
- VPNs can make it easier for your employees to use browsers or mobile phones to access business documents and participate in chat sessions while out of the office.
- VPNs are becoming essential even for workers who need to access their business networks while using public WiFi networks, which are inherently not secure.
- VPNs are important when employees need to get into the corporate network when in hotels, customer locations, or any other WiFi network that your IT department has not secured.
All of those benefits are possible because a VPN creates an encrypted tunnel through the public Internet, so that nobody can intercept the traffic. A VPN also prevents man-in-the-middle attacks.
VPNs are increasingly popular because the Internet is becoming less secure.
Businesses are targeted by malware, by hackers and even by disgruntled employees. A VPN can help offer strong protection to the business’s networks, applications and data.
Launch your business in minutes with GoDaddy Airo™
The lowdown on VPNs
Indeed, modern VPN hardware and software are easier to deploy and set up than older versions that required a lot of patience and skill to install and configure. You can set up most of today’s VPNs in an hour or less, and it won’t take much effort to keep it running. Windows, Linux and Mac computers, as well as most mobile devices, have the built-in ability to connect to business networks via a VPN.
VPNs are available in several different styles:
- As a traditional hardware appliance that can sit on a table or be installed in a server rack
- As a feature within some other security or network device, like a router
- Even as a cloud-based Software-as-a-Service (SaaS) solution from a managed service provider
There are also a number of free software-only VPNs, such as from OpenVPN.net, that you can set up on an on-premises server in your own offices, or install onto on a hosted or virtual server. Here is a how-to on setting up this OpenVPN.net.
This array of options widens the appeal of VPNs and makes it easier to find the right price point and situation. You might found these VPN reviews in LifeHacker and PC Magazine helping in evaluating your choices.
Unified threat management
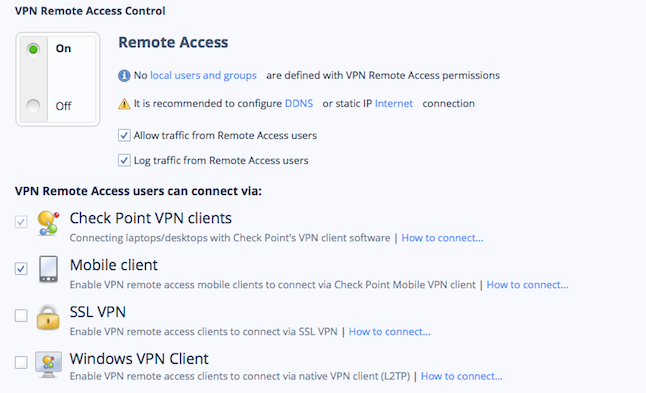
VPNs that used to be the exclusive province of large enterprises can now be found on a variety of security devices, including unified threat management (UTM) tools that combine VPNs with firewalls and Web gateways to offer a range of protective features. A few UTM vendors, such as WatchGuard and Calyptix, have added their own tools, clients, or configuration files to make establishing connections easier. Check Point, for example, has a simple on/off switch to enable its VPN on its UTM appliances, along with a series of Web links for further instructions on how to set up each of its clients, as you can see:
Your choice of VPN will be a function of how many remote users you need to support, whether you already have a network firewall or some other security device that can incorporate or support a VPN, and whether you will feel comfortable with outsourcing your VPN needs to a cloud or managed services provider.
IPsec protocols
In the past, most VPNs came with support for only IPsec (Internet Protocol Security) protocols that were complex to administer and required specialized networking knowledge to set up. Most VPNs these days offer several different alternatives in addition to IPsec, such as Point-to-Point Protocol and Secure Sockets Layer protocols. This makes them more appealing with web applications and a lot easier to install and support.
Which protocol you’ll end up using depends on what kinds of endpoint clients you need to support (such as tablets and smartphones, or simply laptops and desktops) and what activities you’ll be doing over your VPN, such as sharing files from a coffee shop or creating an encrypted link between multiple networks.
As you research VPN products to find the best fit for your business, bear in mind that models are constantly changing; this year’s cutting-edge VPN will next year’s dinosaur. That said, if you choose a current VPN model today, it should be fully functional and secure for years to come, as long as you maintain its software as per the manufacturer’s latest updates. In many cases, that might require an annual support contract.