You've finally got your website running smoothly. Maybe you're selling products, sharing your portfolio, or building your brand online. Then one day, your site suddenly slows to a crawl — or worse, goes completely dark and won’t load. If you've ever experienced this, you might have been the target of a DDoS (Distributed Denial of Service) attack.
Don't worry, you're not alone. Thousands of website owners face this challenge every day, and there are proven ways to help protect your site from DDoS.
Think of a DDoS attack like a traffic jam on the internet highway to your website. Just as a rush of cars can clog a road and prevent regular traffic from getting through, these attacks overwhelm your site with fake visitors, blocking real customers from accessing your content.
Whether you're running an online store or a simple blog, understanding how to prevent and stop DDoS attacks isn't just helpful — it's becoming as essential as having a good password.
In this guide, we'll break down everything you need to know about DDoS attacks and how to defend against them. We'll cover:
- What these attacks actually look like (in plain English)
- How they work (and why they're becoming more common)
- Simple prevention strategies that actually work
- What to do if you're under attack right now
- How to set up long-term protection with GoDaddy Security
The best part? You don't need to be a security expert to follow along. We'll explain everything in clear, practical terms that make sense whether you're just starting out or you're already comfortable with technical concepts.
Pro tip: Even if your site hasn't been attacked, setting up website protection now is like installing a security system in your house — it's better to have it and not need it than to need it and not have it.
Ready to protect your site? Let's dive in.
What’s really happening during a DDoS attack?
Remember that traffic jam analogy? Let's dig a bit deeper into what's actually happening when your site is under attack. Imagine you own a popular coffee shop. On a normal day, customers come in at a steady pace — some ordering drinks, others browsing your merchandise. Your staff can easily handle the flow.
Now imagine if hundreds of people suddenly showed up, not to buy anything, but just to stand in line. Your real customers can't get through the door, your staff is overwhelmed, and eventually, you might have to close shop until the crowd disperses. That's essentially what a DDoS attack does to your website.
The anatomy of an attack
DDoS stands for Distributed Denial of Service, and each of those words matters:
- Distributed means the attack comes from many different sources
- Denial refers to preventing access to your site
- Service is what your website provides to visitors
Unlike other cyber threats that try to break in and steal data, DDoS attacks aim to shut down your site by overwhelming your resources.
Types of DDoS attacks you might encounter
Not all DDoS attacks are created equal. Here are the most common types you might face:
- Volume-based attacks: These are like filling every parking space around your business with cars that never leave. They flood your site with so much traffic that legitimate visitors can't get through. These are the most common attacks because they're relatively simple to execute.
- Protocol attacks: Think of these as people deliberately jamming your door locks with gum. They target the technical handshakes that happen when computers try to connect to your site, exhausting your server's ability to process new connections.
- Application layer attacks: These are the sneaky ones. Instead of just creating traffic, they make requests that look legitimate but are designed to drain your server's resources. It's like having people come into your store and asking your staff increasingly complex questions until they can't help real customers.
How to spot an attack in progress
Your website might be under attack if you notice:
- Your site is unusually slow to load
- You're seeing "Server unavailable" errors
- Some parts of your site work while others don't
- Your hosting company reports unusual traffic spikes
- You're getting complaints from users who can't access your site
Important: Not all slowdowns are attacks. Sometimes high traffic from a successful marketing campaign can look similar to a DDoS attack. The key difference? Legitimate traffic usually builds gradually, while attacks can spike suddenly.
The impact on your website and business
The effects of a DDoS attack go beyond just website downtime. You might experience:
- Lost sales during outages
- Decreased search engine rankings
- Frustrated customers who can't access your services and lose trust
- Additional hosting costs from increased resource usage
- Time and resources spent addressing the attack
- Harm to your company’s reputation
Understanding how these attacks work is your first step toward preventing them.
Tools you can use to help block DDoS attacks
Just as a homeowner needs the right security tools to protect their house, website owners need specific tools to guard against DDoS attacks. Let's look at the essential tools that create a strong defense system for your website.
Web Application Firewall (WAF)
Think of a WAF as your website's smart security guard. It stands between your site and incoming traffic, analyzing each visitor to determine if they're legitimate or potentially harmful. A good WAF will:
- Filter out suspicious traffic patterns
- Block known malicious IP addresses
- Allow legitimate visitors through without delays
- Adapt to new types of threats
Content Delivery Network (CDN)
A CDN works like having multiple copies of your store in different locations. When someone tries to visit your site, they're directed to the nearest location, which helps:
- Spread out traffic across multiple servers
- Reduce the impact of attack attempts
- Improve loading speeds and reduce latency for legitimate users
- Reduce load on hosting resources
- Provide an extra layer of filtering
Traffic monitoring and analysis tools
These tools are like having security cameras for your website. They help you:
- Spot unusual traffic patterns
- Identify potential threats early
- Track where your visitors are coming from
- Measure the effectiveness of your security measures
Load balancers
Think of load balancers as traffic directors for your website. They:
- Distribute incoming traffic across multiple servers
- Prevent any single server from becoming overwhelmed
- Automatically route traffic away from servers under attack
- Help maintain site performance during high-traffic periods
Rate limiting tools
These tools act like bouncers at a club, controlling how many requests can come from a single source. They help:
- Prevent individual visitors from overwhelming your site
- Set reasonable limits on resource usage
- Block automated attack attempts
- Maintain service for legitimate users
The good news? You don't need to source and manage all these tools separately. GoDaddy Website Security includes many of these essential features in one integrated solution, helping create a comprehensive defense system for your site.
Remember: The best tools are the ones you understand and actually use. Start with the basics and add more sophisticated protection as your needs grow. Many of these tools come with automatic configuration options, making them accessible even if you're not a security expert.
Steps to stopping an active DDoS attack
The moment you realize your website is under attack can feel overwhelming. Maybe you first noticed your site slowing to a crawl, or perhaps your customers started calling about error messages. Whatever the warning signs, the key is to stay calm and take systematic action.
Step 1: Check - is it really a DDoS attack?
Before jumping into emergency response mode, take a moment to confirm you're actually dealing with a DDoS attack. Not every outage or slowdown is malicious - sometimes a viral post or successful marketing campaign can create similar symptoms.
Start by checking if the problem affects your entire site or just certain pages. Look for unusual patterns in your analytics, and reach out to your hosting provider for their assessment. Many providers have experience identifying these attacks and can quickly confirm if you're dealing with a DDoS situation.
Step 2: Take immediate action and stop the attack
Once you've confirmed you're under attack, it's time to activate your defenses and enable emergency DDoS protection through GoDaddy's Website Security:
- Log into your GoDaddy account.
- Scroll down to Website Security and Backups and click Manage All ->.
- Find your domain name and click Details under the Firewall heading.
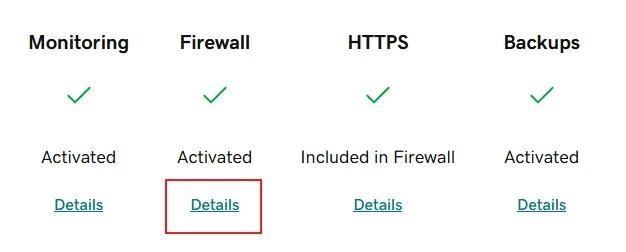
- From the top navigation, click Settings and then select Security from the submenu.
- Click on the Enable Emergency DDoS protection checkbox and then click Save Advanced Security Options to apply the change to your account.
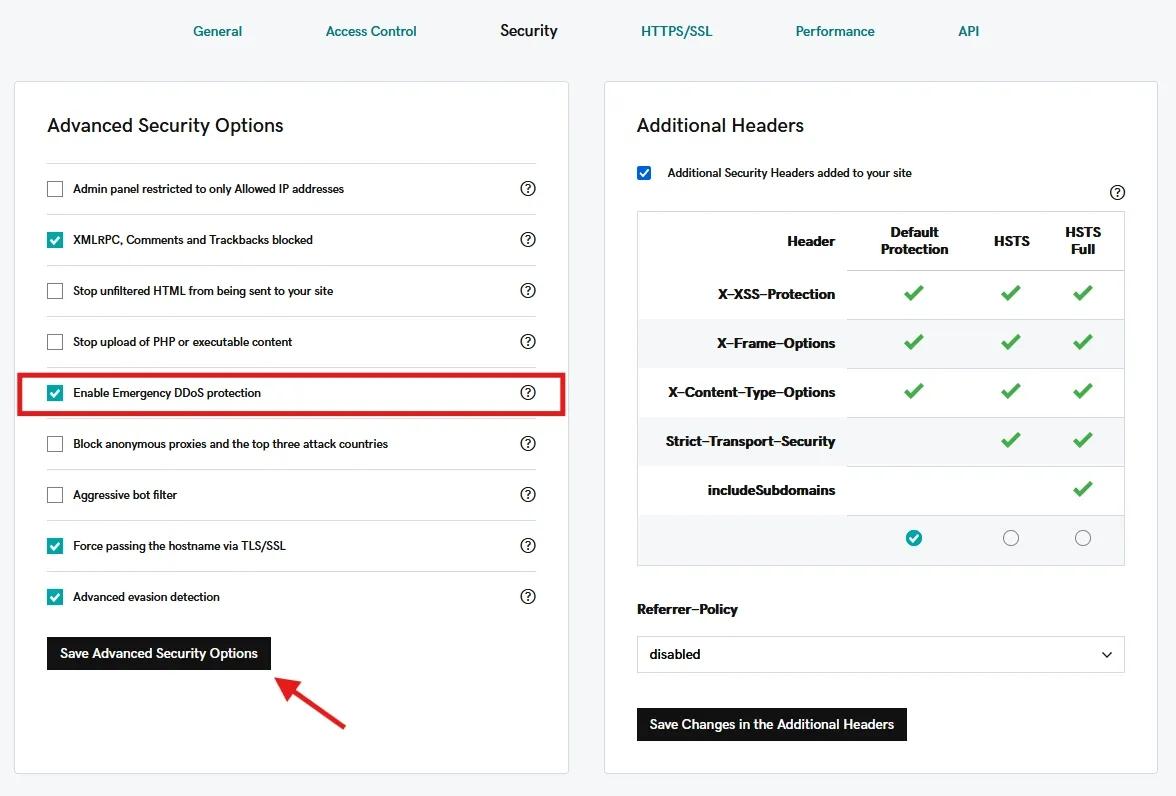
Remember: It can take up to 20 minutes for firewall changes to take effect. During this time, continue monitoring your site's status.
During this time, you may want to work closely with your hosting provider. They've seen these situations before and can often provide valuable insights and additional support. Don't hesitate to ask for help if you need it!
Step 3: Fine-tune your defense
While your initial protection measures are taking effect, you can strengthen your defense by adjusting specific firewall settings. Consider temporarily lowering maximum upload sizes to reduce server strain. If you notice the attack coming from specific geographic regions, you might want to implement temporary geographical restrictions.
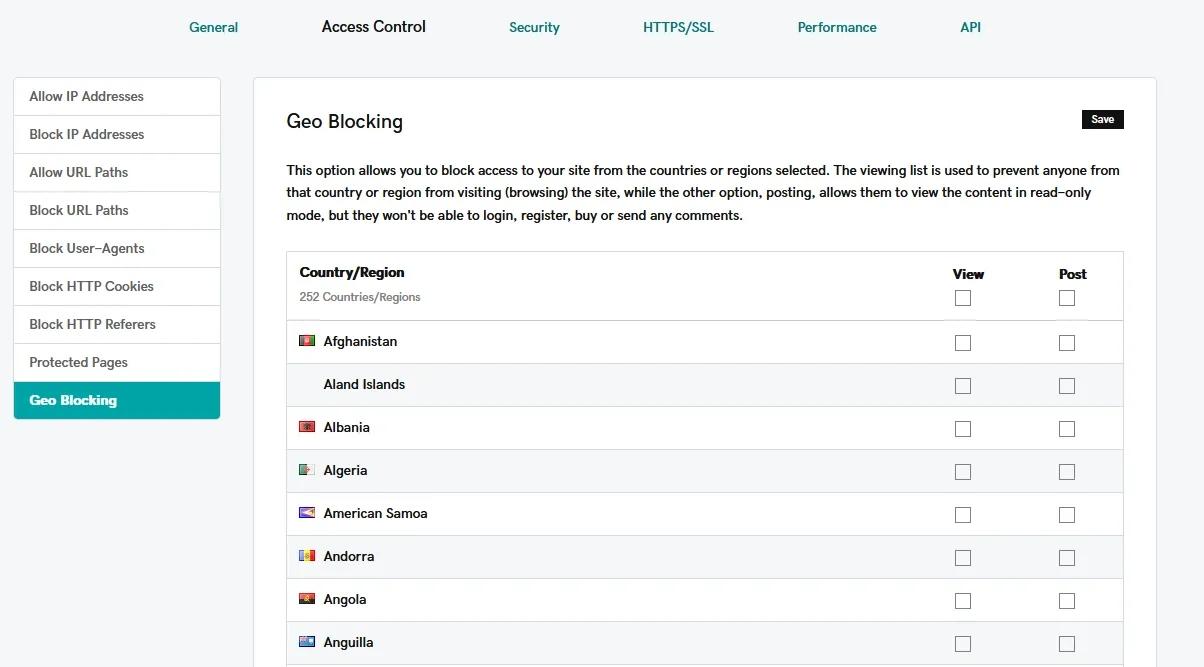
Keep detailed notes about any changes you make during this process. When things calm down, you'll want to review these adjustments to determine which ones should become permanent parts of your security strategy.
Step 4: Keep your audience informed
Communication is really important during an attack. Your customers may need to know what's happening, but be careful about how much technical detail you share publicly. Post general status updates on your social media channels, and consider sending email updates if the outage is significant.
Step 5: Watch for the all-clear
DDoS attacks often come in waves. The initial attack might subside, only to resume hours or days later when you've lowered your guard. That's why it's important to maintain enhanced security measures for at least 24 hours after the attack appears to stop.
Monitor your website traffic patterns carefully during this time, looking for any signs that the attack might resume.
Preventing DDoS attacks before they start
Here's the good news: while DDoS attacks are becoming more sophisticated, so are the tools to prevent them. Think of it like building a castle — you want strong walls (your firewall), a moat (traffic filtering), and guards who know the difference between friends and foes (security monitoring).
Building your first line of defense
Before we dive into the technical solutions, let's establish some basic protection that every website needs:
The basics matter more than you might think. Many successful attacks target sites that skipped these fundamental security steps.
Keep everything updated Just like you update your phone's apps, your website's software needs regular updates. This includes:
- Your content management system (like WordPress)
- Any plugins or themes you're using
- Server software (if you're managing your own)
You’ll also want to monitor your traffic patterns. Get to know what "normal" looks like for your site. How many visitors do you typically get? What times are busiest? When you know your patterns, unusual spikes become easier to spot.
And while website backups won't prevent a DDoS attack, they're crucial for quick recovery. Think of them as your insurance policy — you hope you'll never need them, but you'll be grateful to have them if you do.
Setting up website DDoS protection
This is where GoDaddy's Website Security comes in. Let's walk through setting up your protective shield.
First, access your security dashboard:
- Log into your GoDaddy account.
- Head to My Products and scroll down to the All Products and Services section.
- Expand Website Security and Backups and select Manage next to your domain.
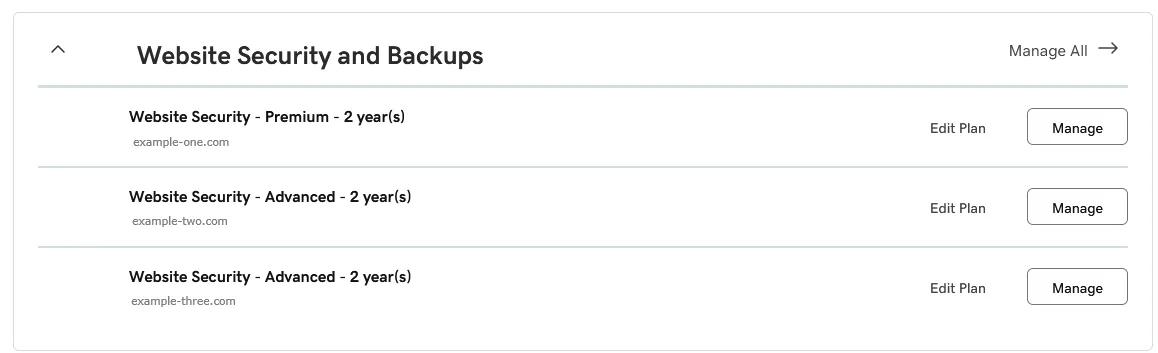
- Click Details under the Firewall heading.

Configuring your Website Security firewall settings
Think of your firewall as your website's bouncer — it needs clear instructions about who to let in and who to keep out. Getting these settings right is crucial for maintaining strong protection while ensuring legitimate visitors can access your site smoothly.
Managing your IP addresses
The foundation of your firewall configuration starts with proper IP address management. Begin by adding your legitimate IP addresses to the allowlist. This tells your firewall which connections to trust automatically.
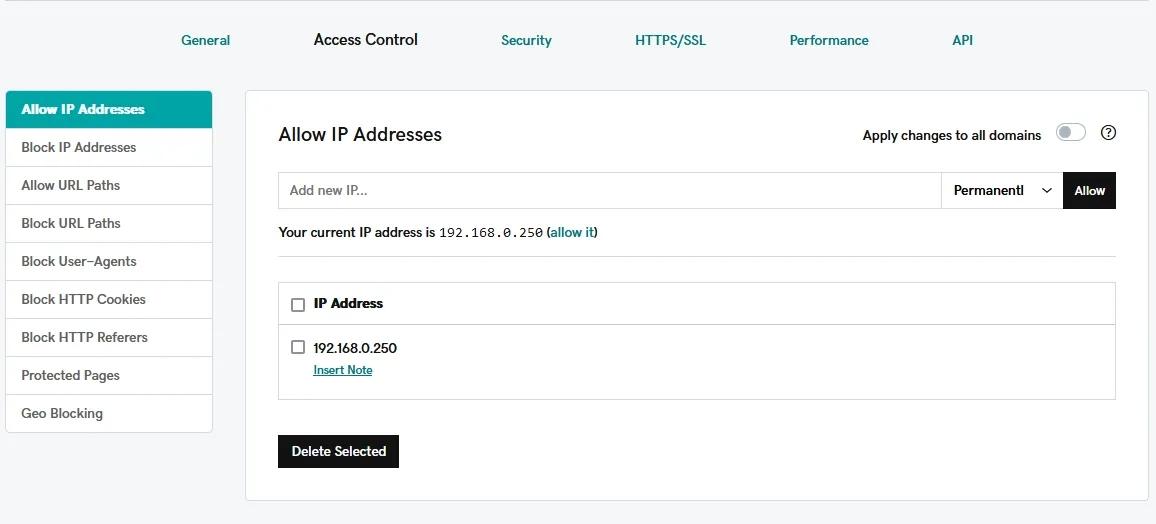
When you need to make changes to your IP configuration, follow this golden rule: always add the new IP address before removing the old one. Your system needs at least one active IP to function properly, and following this order ensures you won't accidentally lock yourself out.
For additional peace of mind, consider setting up backup IPs for failover protection. This creates a safety net for your site, ensuring it stays accessible even if your primary IP encounters issues.
Setting up smart traffic rules
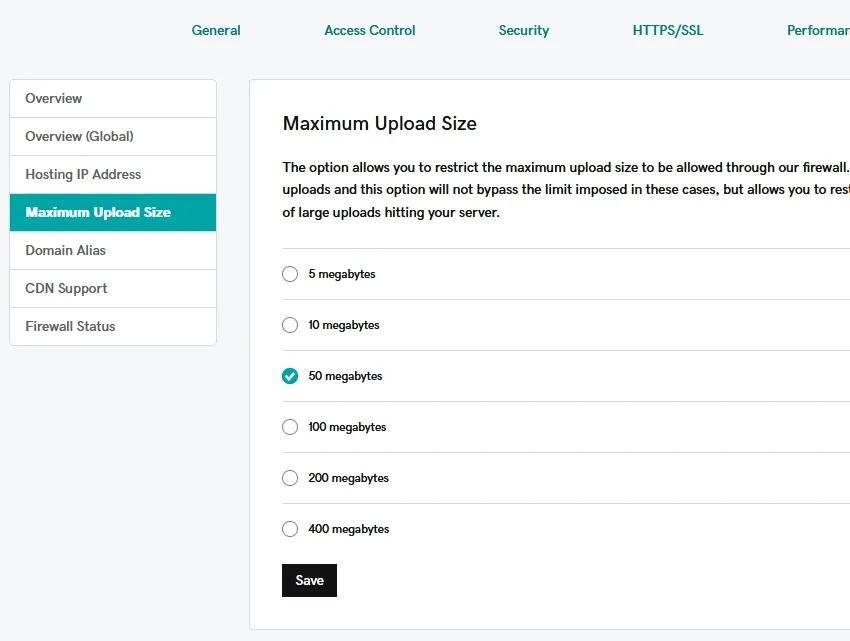
Your firewall's effectiveness depends largely on how you configure its traffic rules. Start by setting appropriate maximum upload sizes to prevent attackers from overwhelming your system with large files.
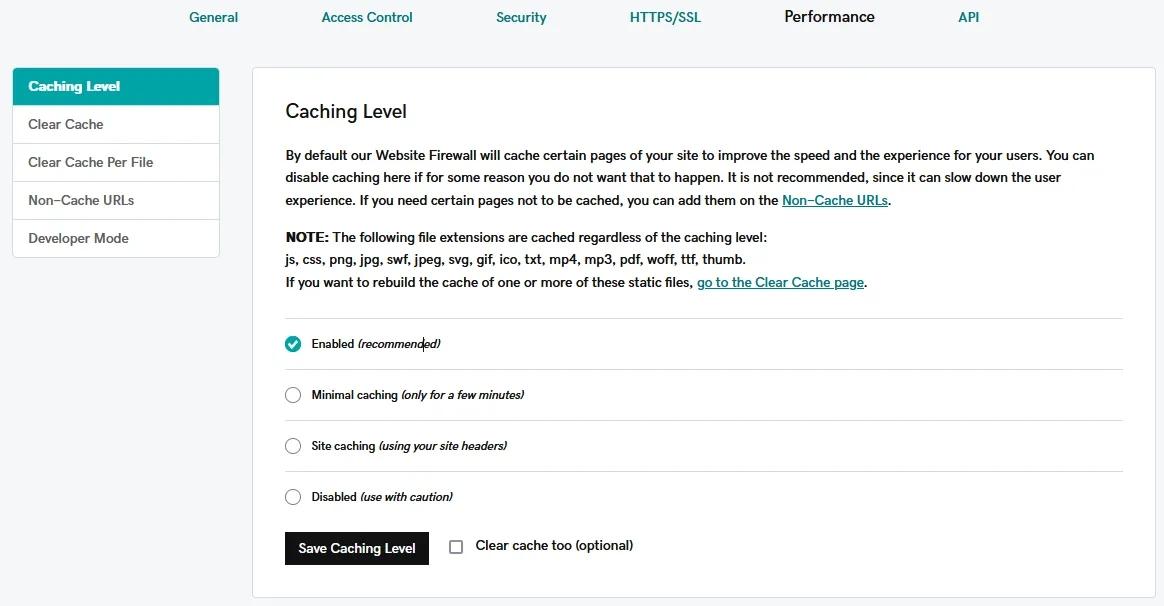
Advanced users can also implement cache rules via the Performance tab that can help reduce the load on your server while improving response times for legitimate users.
The GoDaddy Firewall already runs on top of a CDN (Content Delivery Network) that speeds your website by bringing your pages closer to the visitors. The CDN is particularly valuable, as it distributes your traffic across multiple servers worldwide. This not only improves your site's speed but also provides an additional layer of protection against DDoS attacks.
Custom monitoring and alerts
Finally, you’ll want to set up a solid website monitoring system to keep track of your site's security. This should include custom blocklists for problematic IP addresses and carefully configured alert thresholds that notify you of unusual traffic patterns. Real-time monitoring is your early warning system — make sure it's properly configured to alert you when something needs attention.
Long-term protection strategies that make sense for your website
Building lasting security for your website isn't a one-time task - it's an ongoing commitment. But that doesn't mean it needs to be complicated or expensive. Let's explore your options for long-term DDoS protection that align with your budget and business needs.
GoDaddy offers several tiers of Website Security:
Standard
Perfect for personal websites and small blogs, this plan includes:
- Basic website security with daily scans
- Website monitoring
- Website firewall
- 24/7 security monitoring
- SSL certificate
Advanced
Ideal for growing businesses, adding:
- Daily backups
- Advanced DDoS protection
- Malware removal and prevention
- Blacklist monitoring and removal
- 5 malware removals per year for your site
Ultimate Plan
Built for ecommerce and high-traffic sites, including everything in Deluxe plus:
- Priority response time
- Advanced CDN features
- WAF rule customization
- Unlimited malware removal
The plan you choose is just the beginning. Think of your security strategy like maintaining a car; regular check-ups help to prevent bigger problems down the road.
Protecting your website from DDoS: Next steps
You've learned a lot about DDoS attacks — what they are, how to prevent them, and what to do if you're targeted. But knowing and doing are different things. So, let's talk about your next steps.
Start with the basics: If you haven't already, set up website security with GoDaddy. The Standard plan gives you fundamental protection that works while you sleep. As your site grows, you can always upgrade to more comprehensive coverage.
Pro tip: Even basic protection is better than no protection at all.
And remember — you don't have to figure everything out on your own. GoDaddy's support team is available 24/7 to help with security questions and concerns. Whether you're just getting started or dealing with an active threat, we're here to help.
The bottom line? Website security isn't just another task on your to-do list; it's an investment in your online future. Every day your site stays secure is another day your visitors can trust you, your customers can buy from you, and your business can grow.
Ready to protect your site? Visit GoDaddy's Website Security page to explore your options and find the right protection plan for your needs.






