Security is a problem that never really goes away for site owners. The sad reality is that there are armies of bad guys out there, continually waiting to pounce on poorly maintained sites for the purposes of introducing malware, or spreading spam. Early malware detection is critical.
Though the security surrounding WordPress core has never been better, the platform remains an attraction for malware merchants who target sites with poorly coded plugins, or lax update policies. Even if you’re rigorous in following standard security practices, there’s still a risk that your site could eventually be compromised.
Finding out that Google has detected malware on your site is every web pro's nightmare, but it doesn't have to be the end of the world. In this piece, we'll cover a simple common sense approach to mitigate the damage as quickly as possible if you find yourself affected.
1. Don’t panic
As the pros at Wordfence point out in their excellent “Has My Site Been Hacked? How to Check” piece, there are a number of different ways you might receive the bad malware detection news as a site owner. However you’re notified, it’s critical that you don’t panic. You’ll need your wits about you to get out of this mess as quickly as possible.
Begin by quickly reviewing Google’s “Help! My Site Was Hacked!” resource. It’s authoritative, straightforward, and broadly applicable regardless of what the actual problem is. We’ll be referring to it here throughout. Once you’ve done that, notify your hosting partner if they aren’t already aware of the situation.
Next, identify the key people related to the site who will be helping you with the cleanup, and let them know what’s going on. Ideally, this isn’t the sort of process you want to be stuck handling alone.
2. Assume that everything is compromised and quarantine your site
We’ll get onto specific ways of assessing damage in a minute, but it’s important to assume at the outset that everything is potentially compromised. The problem may well ultimately be limited to a particular plugin, but you have no way of knowing how deep the damage goes initially. If you get a malware detection notice, the safest assumption starting off is that your entire stack is now dubious at best.
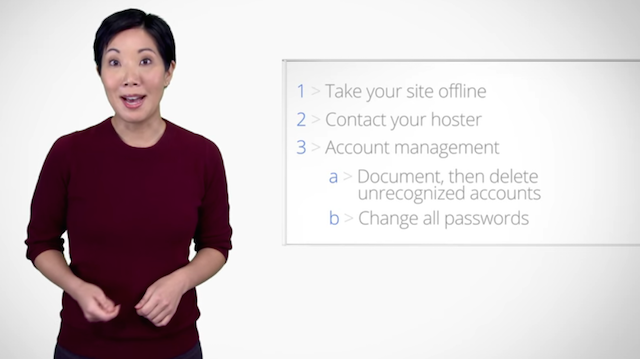
With that in mind, you need to completely lock down your site and place it in quarantine. Follow Google’s quarantine guide for a full breakdown of boxes to tick while you do this. The main points you need to address are:
- Take the site offline so that potentially infected content cannot be served to users.
- Thoroughly vet all system user accounts. Make a note of any illicit account details before deleting them.
- Change all passwords throughout the system.
3. Assess the actual damage
Now the heavy lifting really begins! Again, we’ll stick to the sensible sequence recommended by Google themselves. Start by using the Search Console to determine the nature of the attack. This should help you distinguish between whether you’ve been the victim of a malware or spam incident.

We’ll assume you’re dealing with a malware attack here, but Google also have a solid overview of assessing spam damage. Start actually assessing the extent of the malware hack by following Google’s recommended sequence:
- Prepare thoroughly, and make sure you’re set up to document your findings as you go.
- Dig into the specific malware types you’re dealing with.
- Assess damage to the wider filesystem.
You’ll then want to identify exactly what led to the problem in the first place. Again, Google has your back here. Step through their vulnerability identification guide to investigate root causes such as infected local machines, weak passwords, and out-of-date software.
4. Clean your site
You’ll find an extremely detailed breakdown of actions to take on Google’s guide to cleaning and maintaining your site, including strategies for dealing with user data, and different types of available backup scenarios.
Bearing in mind our second point from earlier, there are a number of issues that are worth stressing strongly here:
- Start with a fresh server install. Ideally, you want a complete break from the previous infected environment.
- Only transfer database information from a backup you know is from before your site was compromised.
- Use completely fresh versions of WordPress, your theme, and any major plugins used.
- Change all passwords site-wide and server-wide.
- Carefully review Google’s final pre-launch checklist before going live again.
5. Request a review
At this stage, you’re nearly out of the woods. Finish the process by stepping through Google’s procedures for requesting a review of your newly cleaned site. In the case of malware, there are two points to bear in mind when you do this:
- The review should be carried out within a week of being requested.
- If the results are positive, browser and search results warnings should disappear within three days thereafter.
Malware detection: The wrap-up
If everything above seems too daunting, Google’s advice on building a support team is a great place to start in tracking down the right expert to help you. Assuming that you’re up to the challenge yourself, the five steps we’ve covered — grueling as they are — will get you out of the hole. Let’s step through them again:
- Don’t panic: You’ll need a clear head to get this done right.
- Lock the site down: Move your site offline and quarantine, then vet all users and change all system passwords.
- Investigate the damage: Assess the extent of the problem and identify vulnerabilities.
- Clean the site: Reboot your site with as many completely new moving parts as possible.
- Ask for a review: Ask Google to officially review the relaunched site.
Have you been hit by malware, or do you have tips for those who have been? Get in touch via the comments section below and share your experiences!







